Data loss can be catastrophic for any server environment. Whether you’re running critical applications or storing important data on your VPS, having a reliable backup strategy is non-negotiable. Restic offers an elegant solution with its encrypted, deduplicated backups that work seamlessly with S3-compatible storage providers.
In this comprehensive guide, we’ll walk you through setting up automated, encrypted backups for your Ubuntu 24.04 VPS using Restic. You’ll learn how to install Restic, configure it with S3-compatible storage, automate backups with systemd timers, and perform reliable restores when needed.
Prerequisites
Before starting this tutorial, ensure you have:
- Ubuntu 24.04 LTS VPS with root or sudo access
- Minimum 1GB RAM and 2GB available disk space
- S3-compatible storage account (AWS S3, Backblaze B2, DigitalOcean Spaces, etc.)
- API credentials for your S3-compatible storage
- Basic command-line knowledge
Resource requirements: Restic typically uses 200-500MB of RAM during backup operations, depending on your repository size and file count.
Installing Restic on Ubuntu 24.04
Ubuntu 24.04 includes Restic in its default repositories, but we’ll install the latest version directly from the official releases for optimal performance and security features.
Method 1: Install from GitHub (Recommended)
First, download and install the latest Restic binary:
# Download latest restic release
wget https://github.com/restic/restic/releases/download/v0.16.4/restic_0.16.4_linux_amd64.bz2
# Extract and install
bunzip2 restic_0.16.4_linux_amd64.bz2
sudo mv restic_0.16.4_linux_amd64 /usr/local/bin/restic
sudo chmod +x /usr/local/bin/restic
# Verify installation
restic versionMethod 2: Install from Ubuntu Repository
Alternatively, install from the Ubuntu repository:
sudo apt update
sudo apt install restic -yConfiguring S3-Compatible Storage
Create a dedicated configuration file to store your S3 credentials securely:
sudo mkdir -p /etc/restic
sudo touch /etc/restic/s3-credentials
sudo chmod 600 /etc/restic/s3-credentialsAdd your S3 credentials to the file:
sudo nano /etc/restic/s3-credentialsInsert your credentials:
export AWS_ACCESS_KEY_ID="your-access-key"
export AWS_SECRET_ACCESS_KEY="your-secret-key"
export RESTIC_REPOSITORY="s3:your-endpoint/your-bucket-name"
export RESTIC_PASSWORD="your-strong-backup-password"Security Warning: Use a strong, unique password for RESTIC_PASSWORD as this encrypts your entire backup repository. Store this password securely – losing it means losing access to all your backups.
Initializing Your Backup Repository
Initialize a new encrypted repository:
# Source credentials
source /etc/restic/s3-credentials
# Initialize repository
restic initRestic will create an encrypted repository with client-side encryption using AES-256 encryption and Poly1305-AES authentication.
Creating a Backup Script
Create a comprehensive backup script that includes logging and error handling:
sudo nano /usr/local/bin/restic-backup.shAdd the following script content:
#!/bin/bash
# Load configuration
source /etc/restic/s3-credentials
# Set log file
LOGFILE="/var/log/restic-backup.log"
# Function to log messages
log() {
echo "$(date '+%Y-%m-%d %H:%M:%S') - $1" | tee -a "$LOGFILE"
}
# Start backup
log "Starting backup process"
# Perform backup with exclusions
restic backup \
--verbose \
--exclude-file /etc/restic/exclude-list \
/home \
/etc \
/var/log \
/root \
--tag "$(date +%Y-%m-%d)" \
2>&1 | tee -a "$LOGFILE"
if [ $? -eq 0 ]; then
log "Backup completed successfully"
else
log "Backup failed with exit code $?"
exit 1
fi
# Cleanup: keep last 7 daily, 4 weekly, 6 monthly snapshots
log "Starting cleanup process"
restic forget \
--keep-daily 7 \
--keep-weekly 4 \
--keep-monthly 6 \
--prune \
2>&1 | tee -a "$LOGFILE"
log "Backup and cleanup completed"Make the script executable:
sudo chmod +x /usr/local/bin/restic-backup.shConfiguring Backup Exclusions
Create an exclusion list to avoid backing up unnecessary files:
sudo nano /etc/restic/exclude-listAdd common exclusions:
/tmp/*
/var/tmp/*
/var/cache/*
/var/lib/docker/tmp/*
/proc/*
/sys/*
/dev/*
/run/*
/media/*
/mnt/*
*.tmp
*.cache
*.logAutomating Backups with Systemd
Create a systemd service for the backup process:
sudo nano /etc/systemd/system/restic-backup.service[Unit]
Description=Restic Backup Service
After=network.target
[Service]
Type=oneshot
User=root
ExecStart=/usr/local/bin/restic-backup.sh
TimeoutSec=3600Create a systemd timer for daily backups:
sudo nano /etc/systemd/system/restic-backup.timer[Unit]
Description=Run Restic Backup Daily
Requires=restic-backup.service
[Timer]
OnCalendar=daily
Persistent=true
[Install]
WantedBy=timers.targetEnable and start the timer:
sudo systemctl daemon-reload
sudo systemctl enable restic-backup.timer
sudo systemctl start restic-backup.timer
# Check timer status
sudo systemctl status restic-backup.timerTesting Your Backup and Restore Process
Test your backup configuration by running a manual backup:
sudo /usr/local/bin/restic-backup.shList available snapshots:
source /etc/restic/s3-credentials
restic snapshotsTest file restoration:
# Restore specific file
restic restore latest --target /tmp/restore-test --include /etc/hostname
# Restore entire snapshot to directory
restic restore --target /tmp/full-restore Monitoring Backup Health
Create a simple monitoring script to check backup status:
sudo nano /usr/local/bin/check-backups.sh#!/bin/bash
source /etc/restic/s3-credentials
# Check repository integrity
restic check --read-data-subset=5%
# Show latest snapshots
echo "Recent snapshots:"
restic snapshots --last 5Best Practices
Follow these security and optimization guidelines:
- Test restores regularly: Schedule monthly restore tests to verify backup integrity
- Monitor backup logs: Set up log monitoring to catch backup failures early
- Secure credential storage: Consider using HashiCorp Vault or similar for credential management in production
- Network considerations: If using dedicated CPU VPS, backup performance will be more consistent
- Storage optimization: For large datasets, consider filesystem choice impact on backup performance
- Bandwidth management: Schedule backups during low-traffic periods to minimize impact
Security Enhancement: For sensitive workloads, consider using confidential computing features to protect data in memory during backup operations.
Conclusion
You’ve successfully implemented an automated, encrypted backup solution using Restic on Ubuntu 24.04. This setup provides enterprise-grade data protection with client-side encryption, deduplication, and flexible retention policies. Your VPS data is now protected against hardware failures, human errors, and security incidents.
The combination of systemd automation and S3-compatible storage ensures your backups run reliably while keeping costs manageable through deduplication. Regular testing and monitoring will help maintain the integrity of your backup strategy.
For production environments requiring high availability and performance, consider Onidel VPS in Singapore with high-availability NVMe storage and automatic backup features to complement your custom Restic setup.


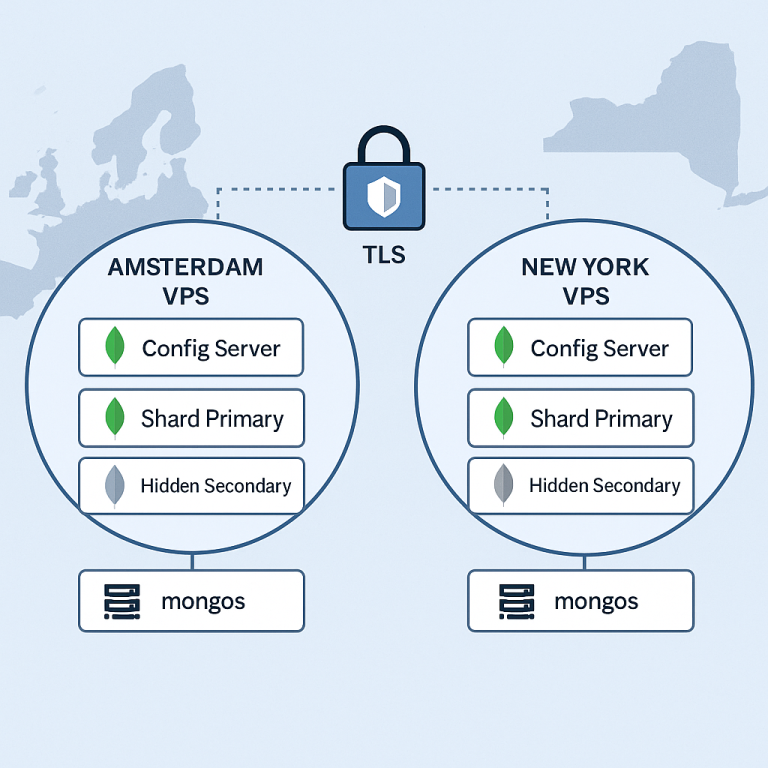
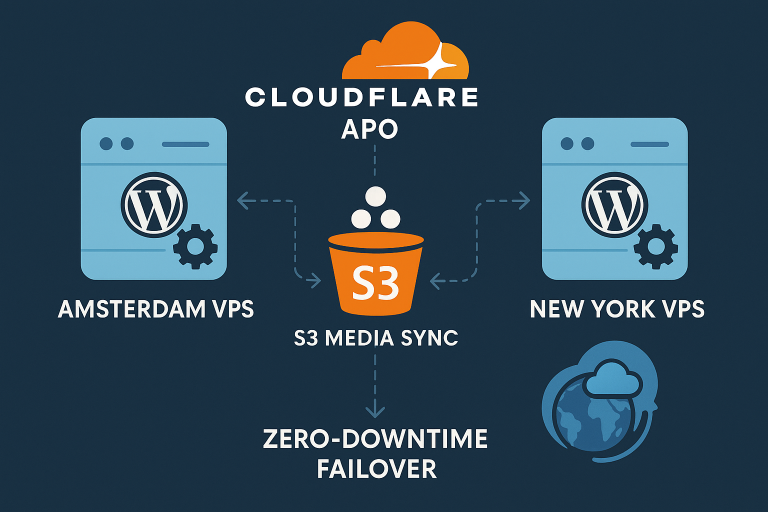
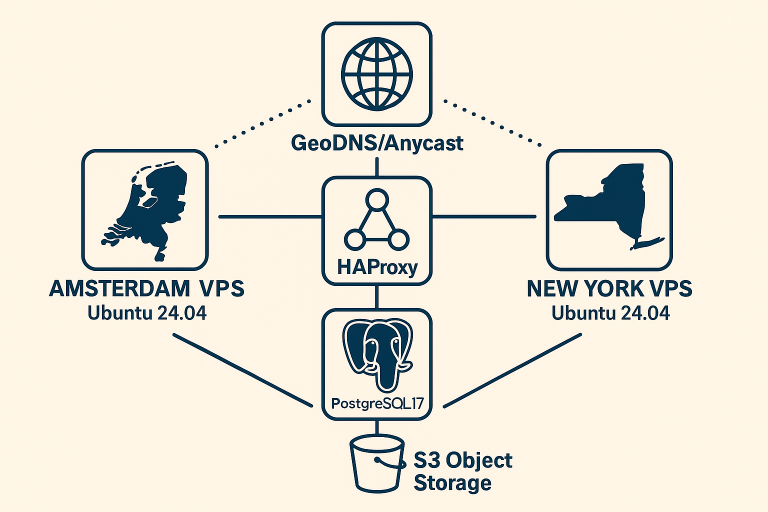

[…] automated backup strategies for rollback […]
[…] VPS deployments, consider implementing automated encrypted backup solutions that can securely store database backups in remote […]
[…] compatibility ensures existing backup tools like Restic work seamlessly across all platforms without […]
[…] the end of this guide, you’ll have a robust, S3-compatible storage cluster suitable for VPS backups, application data, and enterprise […]
[…] proper backup strategies with automated encrypted backups using tools like Restic or […]
[…] Best for: Single-node applications requiring robust backup strategies and disaster recovery capabilities, particularly when combined with automated backup solutions. […]
[…] implementing automated backups using encrypted VPS backup solutions for comprehensive […]