Teleport vs Tailscale SSH vs Cloudflare Access on VPS in 2025: Zero‑Trust SSH, Latency Benchmarks, Session Recording, SSO/Audit, and the Best Choice for Teams
Securing SSH access to cloud infrastructure has evolved far beyond traditional key-based authentication and VPN tunnels. With the rise of zero-trust security models and remote-first teams, organizations need modern solutions that combine security, user experience, and operational efficiency. This comprehensive comparison examines three leading approaches: Teleport, Tailscale SSH, and Cloudflare Access, helping you choose the right solution for your VPS infrastructure in 2025.
Understanding Modern SSH Access Solutions
Traditional SSH access relies on long-lived keys, jump hosts, and complex firewall rules. Modern zero-trust solutions eliminate these pain points by implementing identity-based access controls, short-lived certificates, and encrypted peer-to-peer connections. Each platform takes a different architectural approach:
- Teleport: Identity-aware proxy with comprehensive session recording
- Tailscale SSH: WireGuard-based mesh network with SSH certificate authority
- Cloudflare Access: Global edge-based authentication with browser proxy
Architecture and Deployment Models
Teleport Infrastructure
Teleport operates as a centralized proxy cluster that sits between users and target servers. It requires deploying Teleport Auth Service (certificate authority), Proxy Service (user-facing gateway), and SSH Service (on each target node). Resource requirements typically include:
- Auth Service: 2 vCPUs, 4GB RAM minimum
- Proxy Service: 2 vCPUs, 2GB RAM per 1000 concurrent sessions
- SSH Service: Minimal overhead (~50MB RAM per node)
Tailscale SSH Mesh Networking
Tailscale SSH leverages the existing Tailscale network mesh to enable direct peer-to-peer SSH connections. It eliminates the need for a centralized proxy by using WireGuard tunnels and a distributed certificate authority. Each node runs the lightweight Tailscale daemon (typically 20-40MB RAM usage).
Cloudflare Access Edge Architecture
Cloudflare Access uses a browser-based proxy model where SSH connections are proxied through Cloudflare’s global edge network. It requires installing the cloudflared daemon on target servers (minimal resource overhead) and routes traffic through Cloudflare Tunnels.
Performance and Latency Analysis
Connection latency varies significantly based on each solution’s routing approach:
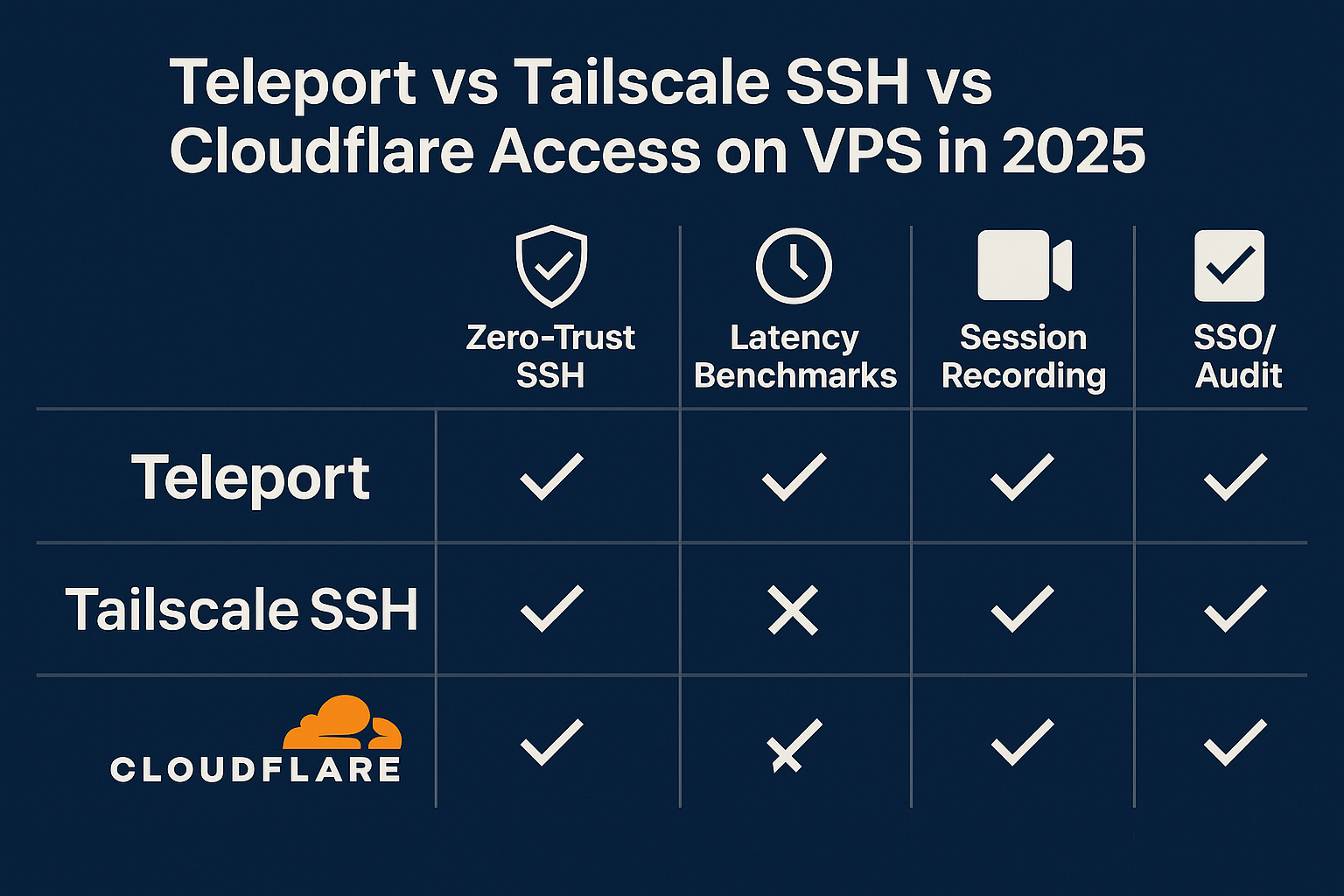
- Tailscale SSH: Direct peer-to-peer connections provide the lowest latency, typically adding 1-3ms overhead for WireGuard encryption
- Teleport: Proxy-based architecture adds 5-15ms depending on proxy location and load
- Cloudflare Access: Edge routing can add 10-50ms, but benefits from Cloudflare’s global network optimization
For bandwidth-intensive operations like large file transfers, Tailscale’s direct connections significantly outperform proxy-based solutions. However, Cloudflare’s edge optimization can improve performance for geographically distributed teams.
Zero-Trust Security Features
Authentication and Authorization
All three platforms support modern identity providers and eliminate long-lived SSH keys:
- Teleport: Comprehensive RBAC with resource-specific permissions, supports SAML/OIDC/GitHub SSO
- Tailscale SSH: ACL-based controls with support for OIDC providers, group-based access policies
- Cloudflare Access: Policy-based access with extensive identity provider integrations
Certificate Management
Each platform handles certificate lifecycles differently. Teleport and Tailscale issue short-lived SSH certificates (typically 1-12 hours), while Cloudflare Access relies on its edge authentication model without traditional SSH certificates.
Session Recording and Audit Capabilities
Teleport provides the most comprehensive audit capabilities with full session recording, command logging, and playback functionality. Sessions are recorded at the kernel level and stored with searchable metadata.
Tailscale SSH offers basic connection logging and can integrate with system audit tools, but lacks built-in session recording capabilities.
Cloudflare Access provides connection logs and basic audit trails through Cloudflare’s logging infrastructure, with limited session recording options.
Operational Complexity and Maintenance
Implementation complexity varies significantly:
- Tailscale SSH: Simplest deployment with minimal infrastructure requirements
- Cloudflare Access: Easy setup leveraging existing Cloudflare services
- Teleport: Most complex but offers granular control and enterprise features
Cost Considerations and Scaling
Pricing models reflect different value propositions:
- Tailscale: Per-user monthly pricing, free tier for personal use
- Cloudflare Access: Per-user monthly pricing with Cloudflare Zero Trust bundle
- Teleport: Enterprise-focused pricing with self-hosted and cloud options
For small teams managing multiple VPS instances, Onidel VPS in Singapore or other regions can benefit from Tailscale’s simple per-user model. Enterprise environments with strict compliance requirements often justify Teleport’s higher costs.
Use Case Recommendations
Choose Tailscale SSH for small to medium teams prioritizing simplicity and performance. It excels when managing distributed VPS clusters or development environments.
Choose Teleport for enterprises requiring comprehensive audit trails, session recording, and fine-grained access controls. Essential for regulated industries and large-scale infrastructure.
Choose Cloudflare Access for teams already using Cloudflare services or requiring browser-based access without local tooling.
Integration with Modern Infrastructure
Modern VPS deployments often involve container orchestration, configuration management, and Infrastructure as Code. Each solution integrates differently:
- Tailscale integrates seamlessly with Terraform/OpenTofu and container environments
- Teleport provides extensive APIs and integrates with CI/CD pipelines
- Cloudflare Access works well with existing Cloudflare infrastructure automation
Conclusion
The choice between Teleport, Tailscale SSH, and Cloudflare Access depends on your organization’s specific requirements for security, performance, and operational complexity. Tailscale SSH offers the best balance of simplicity and performance for most teams, while Teleport provides enterprise-grade features for organizations with strict compliance needs. Cloudflare Access serves well for teams seeking browser-based access within the Cloudflare ecosystem.
Consider evaluating these solutions in your VPS environment to determine which best fits your team’s workflow and security requirements. Each platform offers trial periods or free tiers to test functionality before committing to a long-term deployment strategy.
Related Articles

Top CDN Providers for VPS in 2025: Complete Performance Analysis of Cloudflare vs Fastly vs Bunny vs Akamai
Master Cloud-Init on Ubuntu 24.04: 30 Production-Ready Templates for Docker, SSH Security, and VPS Automation
